Describe Traffic Analysis and Identify Common Uses
Network traffic analysis is primarily done to get in-depth insight into what type of trafficnetwork packets or data is flowing through a network. Detecting the use of vulnerable protocols and.
:max_bytes(150000):strip_icc()/dotdash_Final_Common_Size_Income_Statement_Oct_2020-01-f6706faee5644055954e9e5675485a5e.jpg)
Common Size Income Statement Definition
These data can be an invaluable resource for detecting and isolating.
. Which people spend the most money on your site and are most loyal to your brand. They can assist in network troubleshooting by detecting and diagnosing network problems such as addressing errors and protocol configuration mistakes. Detecting malware such as ransomware activity.
Originally coined by Gartner the term represents an emerging security product category. Website traffic analysis helps you focus on target market segments with the highest conversion and lowest bounce rate to help maximize. For example there is a common pattern of network traffic behavior known as the diurnal curve where traffic usage in a network ramps up at the beginning of the workday at about 830 am.
The database management zone D. NTA systems save network connections data and some systems record raw traffic data. Unlike the User Datagram Protocol UDP TCP is not a fire and forget protocol.
TCP protocol with Wireshark. A network traffic analyzer is designed to capture or log traffic as it flows across the network. Type size origin and destination and.
Who makes up your target market. Network traffic analysis NTA is the process of intercepting recording and analyzing network traffic communication patterns in order to detect and respond to security threats. Two ways to do network traffic analysis.
In general the greater the number of messages observed or even intercepted and stored the more can be inferred from the traffic. The part of the network you dont secure for example a network segment used for visitors to access the internet C. Identify traffic analysis software to use for the evaluation ofeach alternative Determine the specific analysis requirements including but not limited tothe analysis software inputs such as peak hour factor PHF saturation flow rate.
All of these events are gathered by the analytics system and marked with a timestamp and other parameters from the data trace of each website visitor. This occurs when an attacker covertly listens in on traffic to get sensitive information. With network traffic analysis you are able to quickly isolate and identify the who the what and where - in real time.
The idea behind this model is to get very granular concerning the relationship between the adversary hacker and the victim. And continues throughout the day until about 4 pm. Here we analyze the key NTA vendors to be considered by security and risk management leaders.
There are many benefits to traffic analysis but here are three key advantages. Historically this strategy was intended to investigate the sources of all traffic and volumes of throughput for the sake of capacity analysis. Identify what applicationsprotocols are running on the network Identify bandwidth hogs down to a user application or device level Monitor client to server network traffic.
Common use cases for NTA include. Threat hunting helps security teams to detect threats that would go unnoticed by traditional security features. This natural first impulse to observe traffic is actually justified as traffic analysis has proven useful in identifying problems such as configuration errors server performance deterioration latency problems in some of the network components and so many other error conditions.
They also are used for network traffic characterization. SCNM Agarwal03 is a monitoring tool that uses a combination of active and passive measurements to collect information at layer 3 ingress and egress routers and at other significant points within the network being monitored. Is there abnormal traffic.
Protocol analyzers are widely used by network administrators for network monitoring. The traffic statistics from network traffic analysis helps in. Common functionality of analytics systems Collect hit data Any web traffic analytics system collects information about actions on the website registering clicks scrolling form submissions etc.
The network zone where you put servers that serve the outside to limit the exposure. The SCNM environment consists of both hardware and software components. Isolating High Bandwidth Consumers Bandwidth Utilization Spike Knowing there is heavy usage or a spike in bandwidth is one thing but being able to quickly isolate and identify who or what is causing them is another.
Typically network traffic analysis is done through a network monitoring or network bandwidth monitoring softwareapplication. NTAs can assist in the investigation of past incidents and in threat hunting. If one analyzes major criminal intrusion incidents such as the major data breaches against retailers banks and other institutions holding large amounts of valuable data most of these events have been detected by network traffic analysis.
Top-down where analysts examine broad general patterns of usage within network traffic. The ciphertext length usually reveals the plaintext length from which an attacker can get valuable information. Network traffic analysis for IR.
January 14 2020 by Howard Poston. Followed by a natural drop off at the. An attacker intercepts the data sent by the user for later use.
Traffic analysis is the process of intercepting and examining messages in order to deduce information from patterns in communication which can be performed even when the messages are encrypted. TCP tracks the packets that are sent confirms that they are received and. Network traffic analysis NTA is a method of monitoring network availability and activity to identify anomalies including security and operational issues.
Collecting a real-time and historical record of whats happening on your network. Network traffic analysis involves examining packets passing along a network. Network traffic analysis is one part of security analysis that provides insight into communications between technological assets into how they are being used and how they.
The Transmission Control Protocol TCP is one of the most commonly-used protocols on the internet. Network traffic analysis is a new market with many vendors entering since 2016. In a security context they do it to detect threats such as undetected malware infections data exfiltration denial of service dos attempts unauthorized device access etc.
At a glance this helps with the following. Most importantly the creators of the Diamond Model wanted ways to identify the activity of pivoting. Network traffic analysis and detection is where the protection of the network meets incident response.
The safest part of the network used for the security infrastructure B. An attacker can tap into fibers and obtain this information. Adversary infrastructure capabilities and victim.
The four features in the Diamond Model.

Traffic Symbol Signs And Road Symbols To Facilitate Road Traffic And To Increase Road Safety Through Safety Signs And Symbols Road Safety Signs Traffic Symbols
The Common Size Analysis Of Financial Statements

Take Charge Of Retail Analytics With This Powerful Dashboard Analytics Dashboard Retail Dashboard Examples

Transitional Words Spice Up Writing With Common Core Aligned Activities Teaching Writing Transition Words Transition Words For Essays

Traffic Congestion And Reliability Trends And Advanced Strategies For Congestion Mitigation Chapter 2

17 Content Creation Secrets To Wow Your Readers Convince And Convert Social Media Strat Blog Tips Content Marketing Strategy Marketing Strategy Social Media

Top 4 Data Analysis Techniques Maryville Online

Top 4 Data Analysis Techniques Maryville Online

Writing Objectives Using Bloom S Taxonomy By Sohail Ahmed Taxonomy Blooms Taxonomy Writing
/dotdash_Final_Common_Size_Income_Statement_Oct_2020-01-f6706faee5644055954e9e5675485a5e.jpg)
Common Size Income Statement Definition

What Is Network Analysis A Brief Introduction With Examples By Mengsay Loem Towards Data Science

Active Passive Attacks Definition Differences Venafi

New Product Analysis By Adloonix Analysis How To Find Out Budgeting
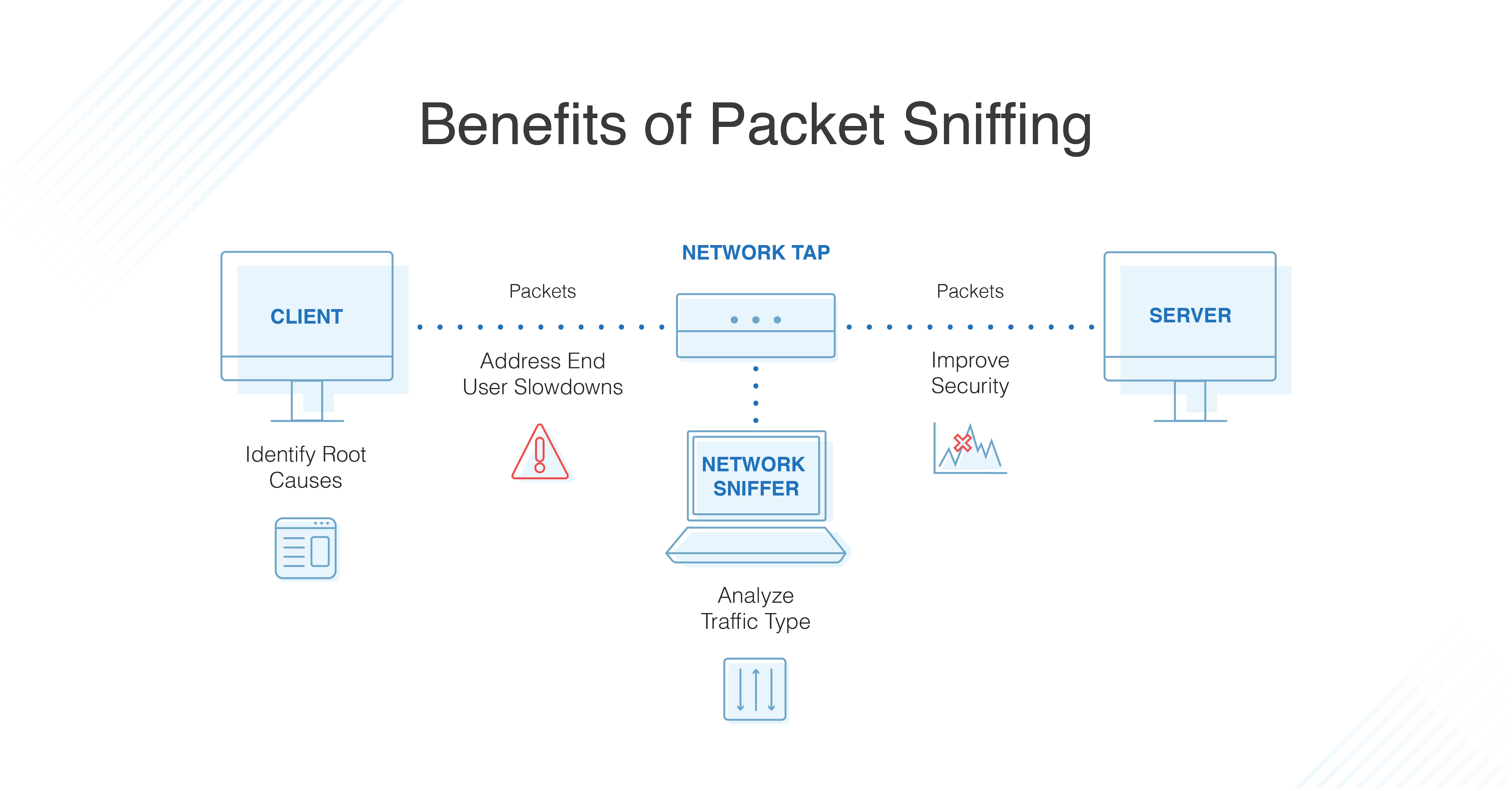
10 Best Packet Sniffers Comparison And Tips Dnsstuff
/dotdash_Final_Most_Commonly_Used_Forex_Chart_Patterns_Jun_2020-01-a6be7f7fd3124918a519946fead796b8.jpg)
Most Commonly Used Forex Chart Patterns

Erni And Iot Projects Iot Projects Smart Traffic Lights Software Projects



Comments
Post a Comment